Blog/Article
How to prevent DDoS attacks and keep your workload flowing

Distributed Denial of Service (DDoS) attacks turned into one of the worst online issues of the 21st century, and finding ways to protect your online services against them became mandatory. This is why your server provider must always keep you safe from harm. More importantly, such protection shouldn't be an extra.
Summary
DDoS attacks are far from impossible to deal with, and every top bare metal provider must be able to keep their customers safe. And for that to be the case, it is fundamental to understand how it all works.
By the end of this article, you will understand how Latitude.sh makes sure you're always safe against these constant threats.
What is a DDOS attack?
The most common DDOS attacks are far from complex. First, imagine a website. Like any digital service or application, it is necessarily hosted on a server, right?
The point of a DDOS attack is to flood the server with malicious traffic and make it impossible for actual users to access whatever they want to access.
Of course, the main consequence is that companies might lose a lot of money in the process since current and potential customers are prevented from reaching what they want to reach.

Even when a business does not lose money because of a DDOS attack, its reputation might be severely affected. After all, the end user might not know if his private information is at risk, for instance.
To make it simple, let's go for an analogy. Imagine a hotel that's fully booked for the weekend. The rooms are all ready to receive them, full of all supplies, and nobody will have to pay for anything.
Now, imagine that, instead of the actual customers, some random teenagers show up and just enter the rooms. They stay there just so no one else can, which obviously frustrates the would-be customers.
The hotel is the server. The rooms are the applications. The invaders are the DDOS attack.
What makes it difficult to prevent a DDOS attack?
You might ask yourself who these attackers are. After all, it takes a lot of people to overload a server (and even more so, if it is a dedicated server).
Are they all real people who gather to strike? Well, sometimes, yes, but not necessarily.
Usually, the attackers control third-party computers that are infected with some kind of malware that allows an invader to give them orders.
These infected computers are what we call bots, and the bots are usually not alone. Just like any hive-minded villain in pop-culture references, these infected computers are interconnected, becoming something called botnets, and fighting them off can be challenging at times.
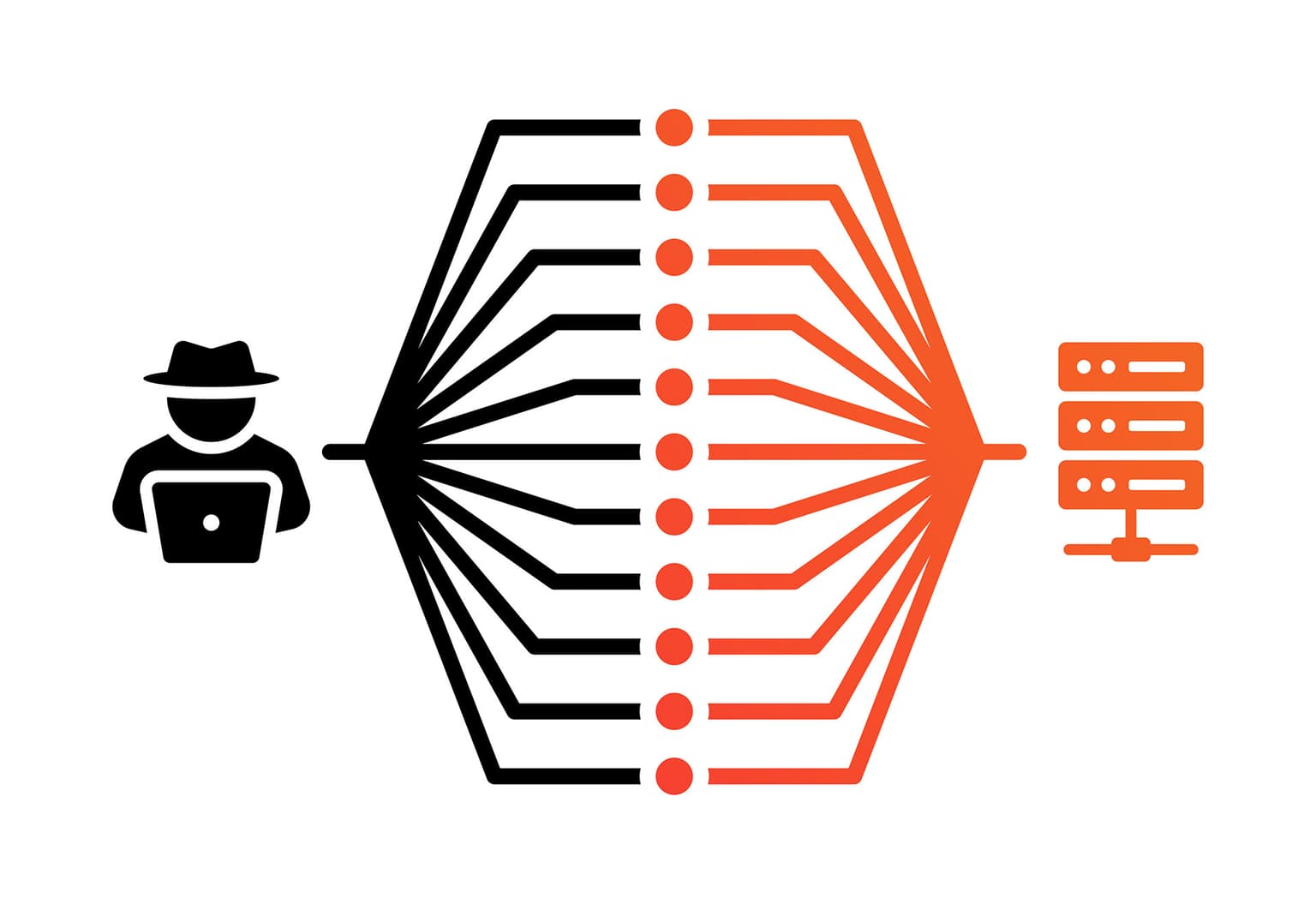
By the way, this is what makes DDoS attacks so tricky. Since the bots can have different IPs, it may take a while for systems to realize the accesses are not legitimate.
There is no automatic internet label that deems IPs as malicious or legitimate. Therefore, specific measures must be taken to ensure these attacks become recognizable and avoidable.
Besides that, we're not talking about a few infected machines. Bots sometimes can reach the thousands or even millions, which is another reason why fighting them is so hard.
When too many IPs start showing similar behavior patterns or your site starts dealing with unexpected peaks in weird moments, you know there is a possible DDOS attack on the way.
Common DDOS attack types
Even though TCP Flood is the most common DDOS attack, which uses different IPs to overflow the server where an application is hosted, there are other types of attacks.
Below, you will find a list of the most common:
UDP Flood: In a UDP flood attack, the attacker bombards the target server with a large volume of UDP packets directed at random ports. As the server receives these packets, it attempts to respond with ICMP "Destination Unreachable" messages for the ports that are not open. This relentless barrage depletes the server's bandwidth and processing resources, which can result in significant service disruptions and outages.
ICMP Flood: ICMP flood attacks use Internet Control Message Protocol (ICMP) packets to overwhelm the target. By flooding the victim with ICMP Echo Request packets (commonly known as pings), the server is forced to reply to each request, which can quickly deplete its resources and bandwidth.
Reflective/Amplified: Reflective and amplified attacks exploit the characteristics of certain protocols, such as DNS and NTP, to generate a much larger response than the initial request. The attacker sends requests with the target's IP address spoofed as the source, causing unwitting servers to flood the target with massive amounts of traffic, leading to service disruption.
Repetitive GET: A repetitive GET request attack targets the application layer by repeatedly sending HTTP GET requests for specific resources. This high volume of requests can overwhelm the server, leading to increased latency and potential downtime as legitimate users struggle to access the application.
Slowloris: Slowloris is an attack that maintains numerous open connections to the target web server for an extended period. It does this by sending incomplete HTTP requests without ever finishing them. This tactic effectively drains the server's available connection pool, ultimately blocking legitimate users from being able to establish their connections.
SlowRead: In a SlowRead attack, the attacker intentionally delays the data transfer, causing the server to wait longer than required for requests to finish. This prolonged waiting period can strain the server's resources, ultimately resulting in diminished performance and accessibility for legitimate users.
Specially Crafted Packet: This form of attack involves sending deliberately malformed or maliciously constructed packets to a server or application. The goal is to exploit specific vulnerabilities in how the system processes these packets, often causing it to crash, freeze, or behave erratically. In some cases, these attacks may allow an attacker to bypass security measures and gain unauthorized access to the system.
Stack Attack: Stack-based attacks target the memory stack of applications, often by overwhelming it with crafted packets. By overflowing the stack buffer, attackers can execute arbitrary code, potentially seizing control of the application or even compromising the entire server. These attacks take advantage of poor memory management and can lead to severe breaches if successful.
Buffer Overflow: Buffer overflow attacks occur when an application writes more data to a buffer than it can hold, causing memory overflow into adjacent areas. This can result in unpredictable system behavior, crashes, or allow an attacker to execute harmful code. Buffer overflows are a common vector for exploiting vulnerabilities and can severely impact the stability and security of a system.
Carpet Bombing: Carpet bombing attacks flood multiple IP addresses within a defined range with massive volumes of packets, instead of zeroing in on a single target. By distributing the attack across various devices, it becomes more challenging to defend against, amplifying the disruption. Beyond overwhelming individual systems, these attacks can cripple network infrastructure, leading to widespread outages. This method often targets entire subnets, causing collateral damage and disrupting services across interconnected systems.
Latitude.sh offers robust protection against several types of DDoS attacks. Unlike to what happens with some public clouds, our specialized DDoS protection does not require any extra payment, it's an integral part of our platform.
All of our customers receive the best possible protection to prevent workload disturbance. Your end users and even yourself might not even realize something bad was ever attempted.
How to stop DDOS attacks
Unlike many providers that offload DDoS protection to third-party services, we at Latitude.sh take pride in managing our own DDoS Protection infrastructure.
This approach gives us full control and visibility over incoming denial-of-service attacks, enabling us to take proactive measures to mitigate them before they disrupt your servers.
Many providers resort to rerouting traffic when under attack, which can lead to frustrating latency issues for you and your users.
At Latitude.sh, we believe that routing isn’t mitigation. Instead of simply changing routes, we actively mitigate attacks right at the source.
Our goal is to ensure your experience remains seamless, with no increase in latency during an attack.
With a staggering capacity of 7 Tbps, our scrubbing centers are equipped to handle any distributed attack, regardless of its shape or form.
Whether it’s a TCP flood or a complex application-layer assault, we’ve got you covered.
Our comprehensive protection includes everything from traditional attacks like UDP and DNS floods to more intricate threats like Slowloris and specially crafted packets.
Also, we believe that security should be accessible. That’s why all our servers come with DDoS mitigation at no additional cost, as previously mentioned, ensuring you’re always protected without hidden fees.
It’s part of our commitment to customer satisfaction and a transparent service experience.
Our DDoS Protection service is fully managed and extends beyond traditional features. With capabilities to block unwanted IPs, manage Access Control Lists (ACLs), and disable unused ports, we take a holistic approach to your security.
Our protection spans layers 3, 4, and 7, creating a comprehensive shield against potential threats.
We understand that communication is key during stressful situations. If we ever encounter an attack that exceeds our capacity, we will null-route the affected IP temporarily, preventing the attack from impacting our network or other customers.
Typically, this route leads nowhere for about two hours, allowing us to regroup and reassess.
Rest assured, our team is always ready to monitor, respond, and keep your infrastructure safe from threats.
If you want to be free of DDOS attacks and keep your workloads flowing, create a free account right now.